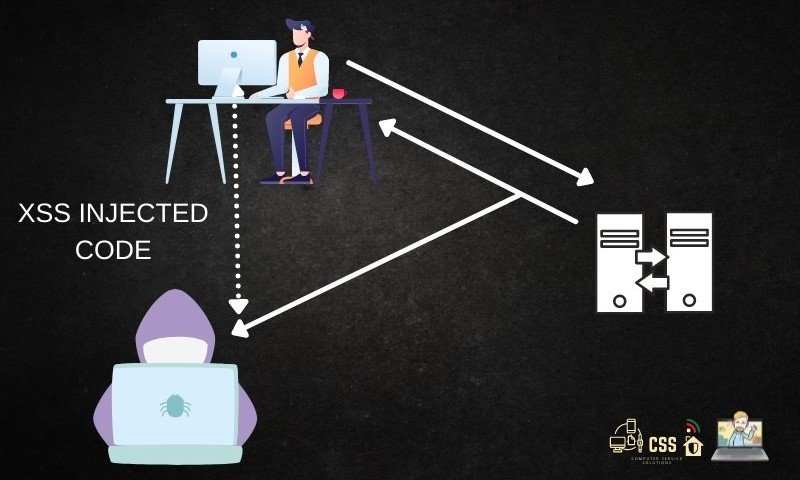
How to check if your PC is hacked? Detect if you someone is tracking you
Have you ever felt like you have been hacked or your system info and data is getting tracked? Do you know what to do next? If not, then this blog post is specifically for you my de
Read More