Simple Mail Transfer Protocol [SMTP (Port 25)]
SMTP was introduced in 1982 as a communication protocol for email transmission. It consists a set of communication guidelines that enable email transmission over the internet. These guidelines include rules for communication between the servers. SMTP also provides the error management feature for incorrect emails.
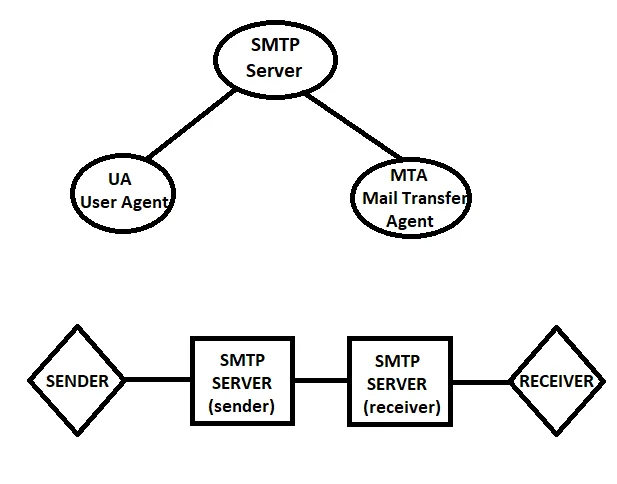
SMTP Server consists of 2 things: UA (User Agents) and MTA (Mail Transfer Agents)
- UA: Used to form a mail.
- MTA: Used to transfer it.
Process of SMTP
- User Agent composes a mail that includes a header and body which is now sent to the SMTP server. Simple Mail Transfer Protocol runs on TCP port 25.
- The header part contains the email address of the receiver having username and domain. This is now sent to Mail Transfer Agent using Mail Submission Agent.
- If the sender and receiver have the same domain, Mail transfer takes place directly. But in case of a different domain, SMTP relay takes place I.e. when mail has to be exchanged from one MTA to another.
- It maps the MX record in DNS records with the target domain. Now the message exchange between servers takes place.
- Finally, after receiving the mail, Mail Delivery Agent (MDA) store it in a mailbox from where the user can retrieve it using the POP3 or IMAP protocol.
Commands:
- HELP: Give all useful info for successful email transfer.
- QUIT: To quit SMTP connection.
- AUTH: For security purpose, Client authentication takes place using Login and Password.
- HELO: Used to start the conversation.
- MAIL FROM: Source email.
- RCPT TO: Email recipient.
- VRFY: Verify if the email exists.
- DATA: Content.
Example
HELO relay.example.com
S: 250 smtp.example.com, OK
C: MAIL FROM: <xyz@example.com>
S: 250 Ok
C: DATA
S: 354 End with .
Content
.
S: 250 Ok
C: QUIT
S: 221 Bye
Different versions of SMTP
There have been several versions of SMTP developed over the years, including:
- SMTP version 1: The original version of SMTP, which was first defined in 1982 in RFC 821. This version of SMTP is no longer in common use.
- SMTP version 2: An updated version of SMTP, which was defined in 1988 in RFC 974. This version of SMTP introduced several new features and improvements, such as support for mailbox names with multiple components, better error handling, and improved reliability.
- SMTP version 3: SMTP defined in 1991 in RFC 1047. This version of SMTP introduced several new features and improvements, such as support for 8-bit data transfer and message size limits.
- SMTP version 4: An updated version of SMTP, which was defined in 1993 in RFC 1425 and 1426. This version of SMTP introduced several new features and improvements, such as support for extended ASCII characters, improved handling of non-ASCII character sets, and support for delivery status notifications.
- SMTP version 5: An updated version of SMTP, which was defined in 2001 in RFC 2821. This version of SMTP introduced support for IPv6, improved handling of email address internationalization and improved security mechanisms.
- SMTP version 6: An updated version of SMTP, defined in 2008 in RFC 5321. This version of SMTP clarified the previous versions and made some minor updates.
Currently, the most widely used version of SMTP is version 5 (RFC 2821) which is supported by most email servers and clients.
Attacks and Security of SMTP
Direct Exposure: Emails are not encrypted and authenticated therefore messages are exposed. This can be secured either by using Secure MIME (Multipurpose Internet Email Extension). Secure Socket layer for SMTP is can help in securing the SMTP without the user`s involvement. Also, PGP (Pretty Good Privacy) minimizes the risk of data exposure.
Account Enumeration: In this attack, the attackers try to gather information about accounts and mailing lists using the account validation methods. To perform account enumeration, attackers use VRFY command through telnet therefore Disabling the VRFY and EXPN command prevents this attack.
Spoofing: SMTP does not include any built-in mechanisms for verifying the authenticity of the sender’s email address. This means that an attacker can easily spoof the sender’s address, making it appear as if the email is coming from a legitimate source.
Phishing: SMTP can be used to send phishing emails, which are designed to trick recipients into providing sensitive information or visiting malicious websites.
Spamming: SMTP can be used to send large volumes of unwanted or unsolicited email (spam). This can be a nuisance for recipients and can also consume bandwidth and server resources.
Relay attacks: SMTP servers can be configured to relay email from external sources, which can be exploited by attackers to send spam or malicious email from the server.
Man-in-the-middle attacks: Because SMTP does not include any built-in encryption, attackers can intercept and read email messages sent via the protocol.
Malware: SMTP can be used to send email with malware attachments. If a recipient opens the attachment, the malware can infect the computer.
Measures to secure your SMTP server and mitigate its security vulnerabilities?
To mitigate these vulnerabilities, it is recommended to use additional security protocols such as Transport Layer Security (TLS) or Secure SMTP (SMTPS) to encrypt email communications, and authentication mechanisms such as Simple Authentication and Security Layer (SASL) to validate the identity of the sender. Additionally, using a spam filter and educating the users to be cautious when receiving emails from unknown sources and never open suspicious attachments or links can also help to reduce the risk of email-based attacks.
Limit relay: Configure the SMTP server to only accept email from authorized sources and limit the ability to relay email from external sources.
Monitor logs: Regularly monitor server logs for suspicious activity and unusual traffic patterns.
Keep software updated: Keep the SMTP server software and any other related software updated to the latest version to ensure that any known vulnerabilities are patched.
Limit access: Limit the number of users who have access to the SMTP server and restrict their access to only the necessary functionality.
Use firewalls: Use a firewall to block unauthorized access to the SMTP server and to restrict incoming and outgoing traffic to only authorized IP addresses.
Intel recently introduced a new technology. To know more, Click here








